___
/\__\
/:/__/_
/::\/\__\
\/\::/ /
/:/ /
\/__/
Eigen Secret
Eigen Secret is a self-custodial private transaction layer for EVM-compatible blockchains, supporting Deposit, Private Send and Private Withdrawal. We enable the users to do internal transfer in privacy pool, which is not enabled in Tonardo Cash.
For the best experience of Privacy on ETH, EigenSecret aims to achieve Decentralizatio. Securit, Privacy-presevation and Easy-to-integrate.
Decentralization: the proofs are generated on user side and the L2 transactions will be stored via DA solution, and this enable everyone can run their own proving node.
Security: the assets are controlled by the user’s account key generated by Metamask or other self-custodial wallets.
Privacy preservation: the Anonymity and transaction data encryption are enabled to preserve user asserts’ privacy.
Easy-to-integrate: the node and web SDK are provided for businesses and end-users to get access eaily.
How it works
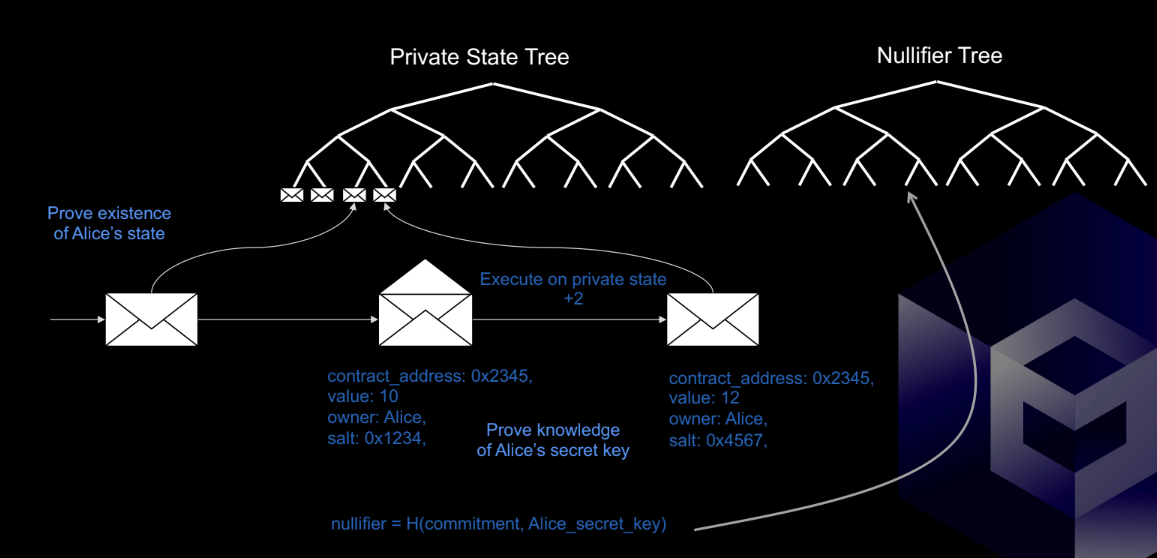
- zk-SMT with UTXO Model
The asset model is built on extended UTXO, each UTXO is attached to a SMT leaf, and also the transition on UTXO is proved by zkSnark.
- Stealth Address
The linkage between sender and receiver is proteced by ECDH, namely Stealth Address. The Stealth Address has been mentioned many times by Vitalik, ERC721 Extension for zk-SNARKs, An incomplete guide to stealth addresses and The Three Transitions.
Here we use one typical digram from above post to do a brief introduction.
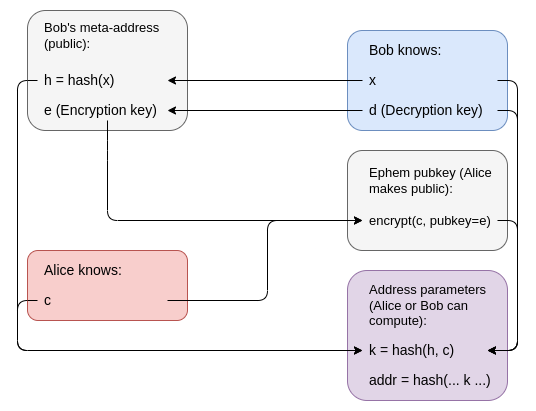
Similarly with classical Key Exchange Protocol, as the basic of TLS/HTTPS, is used to build an encryption communication channel between two individuals without middleman attacks or stealings.
Using a metaphor here, Stealth Address is an alias, and the key of the alias can be derived via your master address’s. Stealth Address is not a new thing, but is pretty much suitable for ETH due to it’s Account Balance Model, the shield EOA by Ring Signature or Encyption Scheme cann’t be verified by ETH node in TXs. The Stealth Address with Snarks is a good solution but still need additional out-of-bound channel to transmit the sender’s public key to receiver(the step d(Decryption Key) -> e(Decryption key) in above diagram) for cutting of the address linkage (anonymity).
EigenSecret uses an account ID/alias as Stealth Address, and binds both L1 and L2 address to the alias. Hence, the users can do send or withdraw to the receiver’s alias with a snark proof to prove the bind relationship.
- Account Recovery
EigenSecret imports an alias, so it supports Account Recovery natually.
The L2 account(we call it Secret Account) has an account key and a signing key, and all are EdDSA key pair currently and are changing to EcDSA meanwhile. the account key is used to hold the users’ asset and the signing key is used to signing the L2 transaction. All the two keys can be upgraded once you found they are compromised.
Once you found the account key leaked, The migrateAccount can be used to replace the old, and mark the old as nullifier and insert the new account into SMT onchain. For signing key upgrade, updateAccount is provided.
The signing key is also used to encrypt the transaction to prevent
- Aggregation Proof
All circuits are implemented by Circom 2 and proved by eigen-zkvm/zkit. The eigen-zkit allow the proof of each transaction being aggregated to decrease the user’s gas cost.
How to use it
Easy-to-integrate and Easy-to-use means developer and user friendly, which is EigenSecet’s design rationale. We provide Web and Node SDK and a very simple UX.
Now EigenSecret is deploy on Scroll Alpha and Polygon Mumbai. Check out the tutoral for a try.
The next step
Transparent Proving: using starkjs on user-side, and recursively prove on server-side, and finally aggreagted and synced to Layer 1.
Data Availability: The L2 transaction would be stored in L1 once EIP4844 supported.
